In Part 1 of MED-V Step by Step Setup Guide, I’ll be concentrate on the prerequisites for MED-V server setup. First of all, we need to enable Web Server IIS role, followed by features like .NET Framework 3.5.1 and BITS. Lastly, we will install SQL Server 2008 SP2 Express Edition.
Open Server Manager, click Roles, and then click Add RolesClick Next on the Before You Begin tab
Tick the Web Server IIS role on the Server Roles tab
Click Next on the Web Server (IIS) tab
Scroll down to the Security section and tick the following services:
- Basic Authentication
- Windows Authentication
- Client Certificate Mapping Authentication
Click Next once you’re done
Click Install on the Confirmation tab
Click Close after the installation finished
Go back to the Server Manager and this time click on the Features option
Tick the .NET Framework 3.5.1 features and BITS. A pop-up windows (Refer to below) will appear once you tick the features.
Click Add Required Roles
Click Add Required Roles
Click Next on the Web Server (IIS) tab
Click next on the Role Services tab
Click Install on the Confirmation tab
Click Close once the installation is done
Next, we will proceed to SQL Server installation. MED-V support both SQL Server 2005 Express Edition and SQL Server 2008 Express Edition. In my case, I'm using the SQL Server 2008 SP2 Express Edition. You can download it here.
After the SQL Server finished the extraction, click on the Installation tab. Select the first option, New SQL Server stand-alone installation or add features to an existing installation
Click OK on the Setup Support Rules page
Click Next on the Setup Support Files tab
Click Next on the Setup Support Rules tab
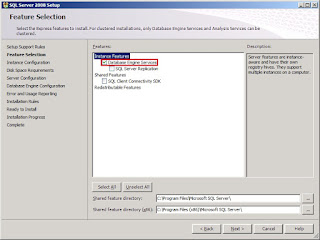
On the Features Selection page, tick the Database Engine Services and then click Next
Click Next on the Instance Configuration tab
Click Next on the Disk Space Requirement page
On the Server Configuration page, select the SQL Server Database Engine Service’ Account Name as NT AUTHORITY\SYSTEM. Click Next after you’re done.
On the Database Engine Configuration page, Account Provisioning tab, select the Authentication Mode as Mixed Mode (SQL Server authentication and Windows authentication). Enter the complex password, P@ssw0rd for my case. Click Add Current User to specify the SQL Server administrators. Click Next once you’re done.
Click Next on the Error and Usage Reporting page
Click Next on the Installation Rules page
Click Next on the Ready to Install page to proceed the installation
Click Next on the Installation Progress page
Click Close once the installation completed
Hooray… You’ve done all the prerequisites already. Next, we will proceed to Part 2: MED-V Server Installation and Configuration. Stay tuned~!!!